 |
|
 |

 |
|
 |

PURPLE was the designation given by U.S. cryptanalysts to the cipher machine used by the Japanese Foreign Office for secure communication before and during the Second World War. Analogs of the PURPLE machine, like the one shown above, were used by the Allies to decrypt those messages.
The structure and internal wiring of the machine, as
well as details of the keying procedures and systems of abbreviations used
in PURPLE messages are described in the paper:
Freeman, Wes., Geoff Sullivan, and Frode Weierud. 2003.
PURPLE Revealed: Simulation and Computer-Aided Cryptanalysis of Angooki Taipu B ,
Cryptologia, 27(1) 1‐43.
Because there is still a considerable interest in the PURPLE cipher machine and how it was broken I have decided to slowly release here copies of some of the documents we used when we analysed the machine and wrote our Cryptologia article in 2003.
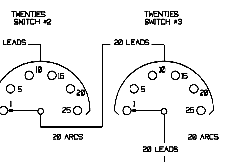 |
How it worksClick on the block diagram for a quickexplanation of how the PURPLE machine works. |
 |
Do it YourselfLearn how to decipher an actual PURPLEmessage. This is part 1 of the 14-part message which was delivered to the U.S Government on December 7, 1941. Click on the image of the message to view the complete image and get instructions on how to decipher the message with a PURPLE simulator. |
The graphical PURPLE simulator is available for use with Windows 3.1x, NT4, 95, 98 and 2000.
A command line Automated Cryptanalysis Program for the PURPLE cipher, for use with 32 bit variants of the above operating systems is also available.
Update: This little command line tool has recently been tested to work
in the Command Prompt of Windows 10. Please see the updated text file in the new ZIP archive for more information. CCR, July 2020.
Here are transcripts of the intercepted text of part 1 and also
part 5 of the 14 part message from Tokyo to Washington, 6/7 December 1941.
The transcript of a super-enciphered PURPLE message from 1941 can be found here.
| Back to Frode’s CryptoCellar | Back to Simulator Index |
Site visitors: